So recently, I signed up for PWK Lab access from 7 November 2021 to 6 January 2022. However, one thing that I noticed is that resources on how to use the labs are quite badly scattered around. The official resources are hidden in the FAQ, scattered in different articles. There are some good articles by the community with helpful tips but all their suggestions are also scattered. Today what I'm going to try doing is to consolidate what you need to know when you get your lab access.
I originally had some plans of what to do, but then Offsec just like, Here is the new exam! Now AD is tested and stuff! Yay! Totally didn't ruin my plans at all
Everything in this article can be found freely online without needing access to the paid course material.
Who is this article for
I mainly decided to write this as when I gained access to the PWK labs, I was unsure what to do and where to start. Hence, I want to gather all the key details you should know when you receive your connectivity package.
Buying the Course
So the first thing you would need to do when starting on your OSCP journey is to, of course, buy the course. You can do that through the official website here
The things you would receive are
- VPN connectivity pack
- Control Panel URL - Very important for managing the network
- ~800 page PDF and Videos
Some things to take note are
- You don't just start lab access right when you bought the course, you have to select from a set of dates. For me, the nearest date (which is the one I chose) was about a month away from the time I bought the course
- Right after that you need to confirm your identity, and check your VPN connection. They will send you emails which are time sensitive so take note
- On the day you start your labs, you receive the course material, which you should immediately download and backup, since the links expire
- You should refer to the FAQ here, and especially the PWK onboarding guide and the OSCP exam guide It provides a lot of important information
Strategies
Some strategies for how best to maximise your course time are
- Jump straight into the labs and hacking the machines from day 1. 1.This strategy I find is most suited for experienced users who have done several machines on HackTheBox/Vulnhub (preferably TJNulls list). If you have not I highly discourage doing this
- Read through the course materials (PDF/Videos), do the course exercises, and then start the labs
- This would probably be best suited for beginners or people with insufficient experience
- It is also what is recommended by Offensive Security themselves.
- Do the labs and the course exercises together.
- This is the strategy I took. Whenever I was stuck at a box, I took some time off to do the course exercises and my lab report
- One good example is here
What strategy you choose depends on your skill level etc. However, I highly encourage at least glancing through the PDF. After all, if you are here to learn, it doesn't hurt to at least see what they offer and fill in some gaps in knowledge.
There are many writeups on OSCP and how to tackle the exam online. Those make for good and entertaining reads, and it would be fine to include them in your strategy. Just don't be stuck on the paradox of choice and the conflict in opinions. One of the writeup I found the best would be John J Hacking's Guide.
Course Materials: PDF and Videos
As many others have stated, the course will give both a 800ish page PDF, as well as many videos.
I mainly just read the PDF and did not touch the videos. However, you should follow whatever style suits you. If videos are a better way for you to learn, you should watch the videos.
The PDF itself is good but there are still areas which are lacking. Here is a list of (hopefully free) resources which can supplement the PDF
- Buffer Overflow
- The PDF's Buffer Overflow content is good enough for guiding you through how to do a basic buffer overflow but ideally you should get more practice.
- TryHackMe's Buffer Overflow Prep Room is a good resource, another good practice is BrainPan
- Privilege Escalation
- Linux: TryHackMe's Linux PrivEsc Room is relatively decent
Lab Report & Course Exercises
Many people in the past say doing all the course exercises is not worth it for just 5 points. After all, the course exercises mainly involve simple tasks such as showing that you followed along, do some modification which is either shown in the book or is easy enough to Google and follow along. And there are a lot a of exercises. It took me about a month (though I also did lab machines alongside it) to finish the exercises.
But now with the new change in exam, the Lab report is now 10 points and a big deal. There are more chances where the 10 points would be able to pull the exam to a pass. (In the past, it has a minimal impact, only helping if you fail to privesc either your 25 pointer or 5 pointer or something along those lines. Now it helps if you fail to gain a foothold/privesc in any one of the 3 exploitable machines). It's still a ton of work, but it is more worth it.
However, there are also other reasons to do the lab exercises. They help to significantly consolidate concepts and fill in some knowledge gaps.
You could use the extra time on the Lab Report to hack more machines and become better at hacking and passing through your own merit. Whether you want to do that or get a safety net is up to you to decide.
For me, I did the lab exercises and read the PDF because I came here not just to get the certification, but also to learn
Client Machines
To help with your lab exercises, you will be given 3 machines to assist you, a Windows Client, Windows Server (in an internal network with the Windows client, not accessible using your VPN normally), and a Linux Client.
On first use I had to reset them before they functioned properly.
You can use remote desktop to connect to your clients (and you can ssh into your Linux client). You can even use tools like evil-winrm to get a shell into your windows client. I used rdesktop to transfer files from my kali VM into my Virtual Machine
Some sample commands
rdesktop <ip> -u admin -p lab -r disk:linux=/home/eaydin/windows
ssh root@<ip>
Lab Access
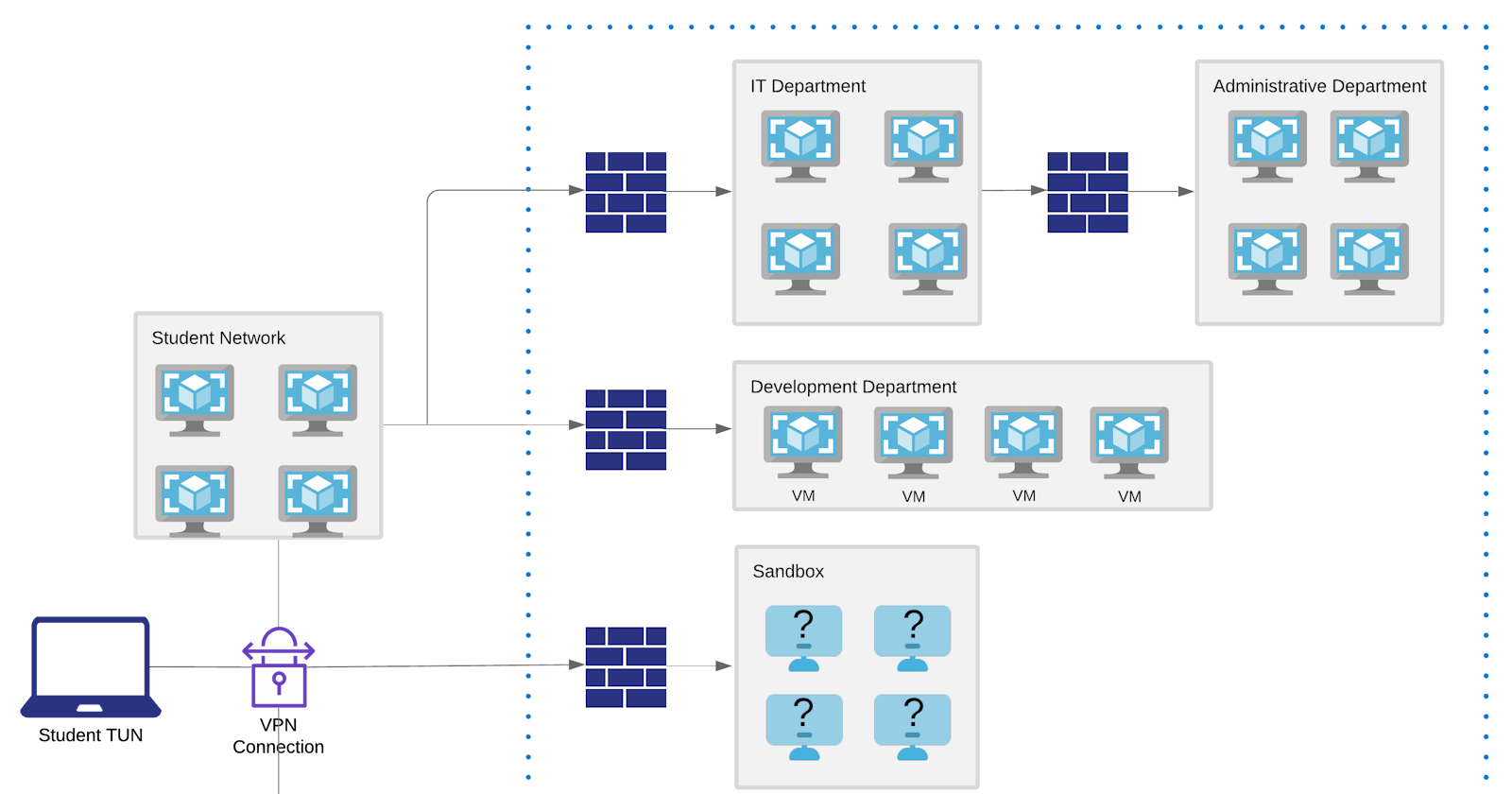
Scenario
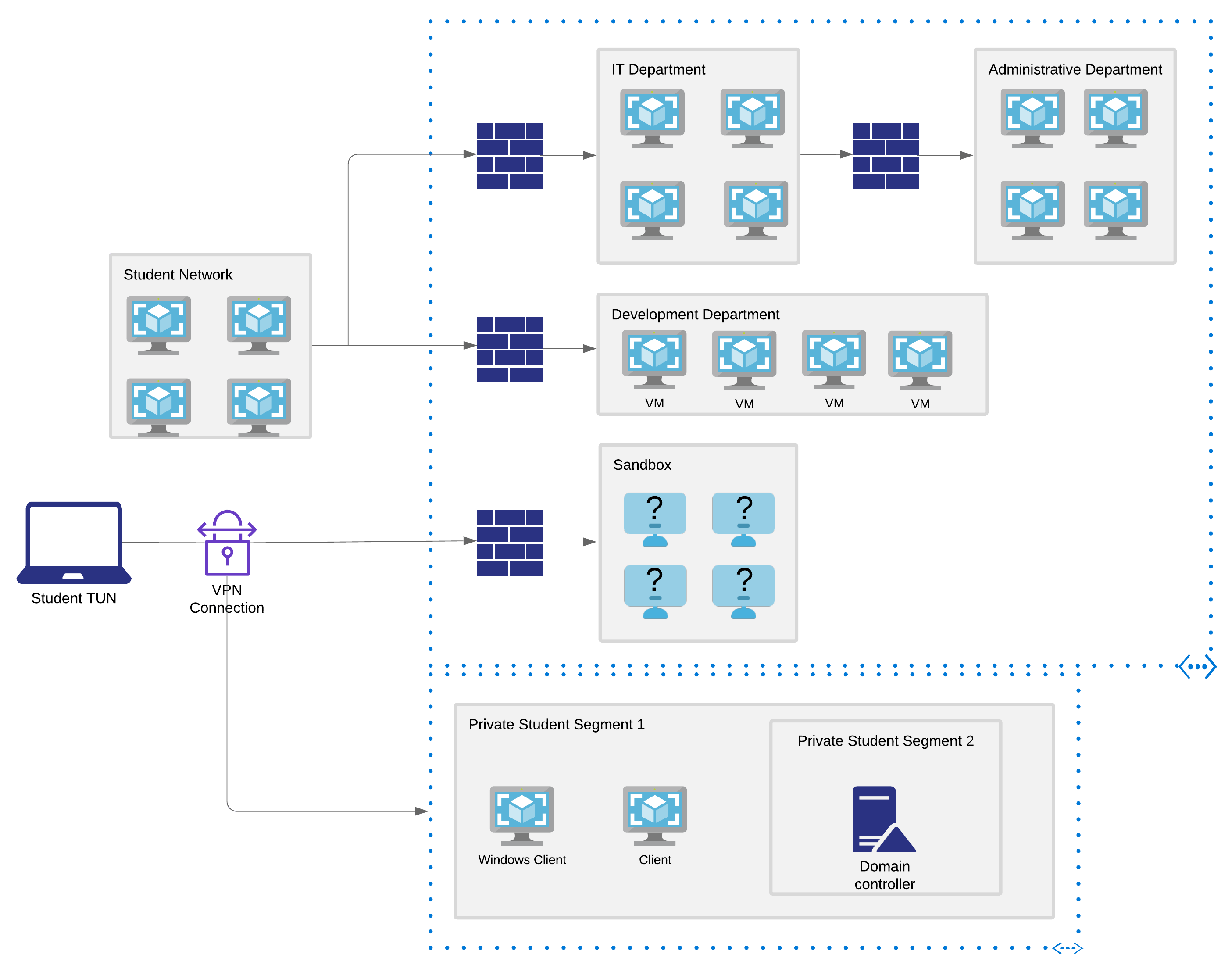
There is a guide that you should read through. The main important takeaways are that
- This is meant to simulate a real network.
- There are dependencies. You would need to enumerate some files. This is NOT just many unrelated CTF boxes.
- There are internal networks, and pivoting too.
Where to start
Before you even start hacking anything, you should know that there is a Learning Path for beginners to follow through. There are also hints you can find on their website.
Once you receive your VPN connection, you can just start scanning the given IP range, which is 10.11.1.1/24, and start hacking!
One Last Thing
Notetaking is going to be essential. It is how you organise your thoughts, learn from past failures, and eventually write your report
Some famous apps are
- CherryTree - Good App, downside is that markdown doesn't work
- Joplin - Markdown note taking app. Has a phone client. I find it does not support hierarchical notes very well. Also the phone client is slow on very long notes (which I often have)
- Obsidian - Also Markdown (though slightly tweaked to allow for easier linking between notes). Can create graph like relations between notes. Has a decent phone app.
Personally what I did was to use Obsidian for Notetaking. I constantly backup (did i mention you should do that for everything, even your VM? ) my vault onto GitLab in a private repo (Thanks John Hammond, that saved my notes many times. If you want to know more about my note taking for ystrategy you can read these resources
TLDR
- Time delay between buy date and receive course materials date
- Read through the onboarding guide
- Choose your strategy wisely, with or without lab report & course exercises?
- Just need to rdesktop/ssh into your client machines. Make sure to reset before first use.
- Read materials/Watch Videos, and start hacking
10.11.1.1/24on your lab network.- If need help starting, follow the PWK Learning Path on their official website
- And take notes along the way!
Next Part
For now that's a long enough article. In the next part of my series, I will be discussing more about how I used my lab time, the upsides and downsides of using hints for the labs and so on.
Who knows, will I fail and give up? Or will I manage to pass on my first try? Only time will tell how this article will age...